
By Rinki Pandey September 12, 2025
Imagine logging into your business bank account and finding thousands of dollars withdrawn via an ACH transfer you never authorized. This nightmare scenario is increasingly common.
ACH fraud – unauthorized or deceptive transactions through the Automated Clearing House network – poses a serious threat to U.S. businesses. In fact, 79% of organizations experienced attempted or actual payment fraud in 2024, and 34% reported incidents of ACH debit fraud.
Small businesses are especially at risk; they often lack the resources and sophisticated controls of larger firms, making them prime targets. The good news is that by understanding how ACH fraud works and implementing effective prevention strategies, you can protect your business’s finances and reputation.
In this comprehensive guide, we’ll explain what ACH payments are, how ACH fraud schemes operate, and practical steps for ACH fraud prevention. All recommendations focus on U.S. regulations and guidelines, ensuring relevance for American small business owners.
You’ll also find visual aids (including a comparison table of fraud types), concise FAQs, and actionable tips to help safeguard your company from ACH payment fraud.
Understanding ACH Payments in the U.S.
ACH (Automated Clearing House) payments are electronic funds transfers between bank accounts, processed in batches through the ACH network. In the United States, ACH is the backbone of direct deposits (like payroll) and direct payments (like vendor payments or bill payments).
These transfers use only two key pieces of information – a bank routing number and an account number – to move money between accounts. Criminals know this, and if they obtain those details, they can initiate fraudulent ACH transactions with relative ease.
How ACH transactions work
When you authorize an ACH transfer (for example, paying a supplier or running payroll), your bank (the Originating Depository Financial Institution, or ODFI) sends the request through the ACH network to the recipient’s bank (the Receiving Depository Financial Institution, or RDFI).
The process typically takes one business day (though same-day ACH is also available), which means there is a slight lag between initiation and final settlement. This delay, while usually just hours, can be exploited by fraudsters in certain schemes like kiting (more on that later).
Importantly, ACH transactions lack some of the real-time visibility of wire transfers, so unauthorized debits might not be noticed until after they post.
ACH payments are convenient and cost-effective – there’s no paper check to handle, and fees are lower than credit card processing. For small businesses, ACH is a lifeline for efficient cash flow management. However, the same features that make ACH convenient can also introduce risk.
For example, anyone with your routing and account number can attempt to withdraw funds via ACH if proper safeguards aren’t in place. Unlike card payments, ACH transfers often don’t require a PIN or face-to-face authentication; they rely on trust and authorized agreements. Fraudsters exploit this trust by using stolen information or social engineering to make unauthorized transactions.
What Is ACH Fraud? (And Why Small Businesses Should Care)
ACH fraud is an umbrella term for scams in which criminals unauthorizedly move money in or out of bank accounts via ACH transactions. This can happen in two main ways:
- Unauthorized ACH debits (withdrawals): A fraudster pulls money from your account without permission.
- Fraudulent ACH credits (payments): A fraudster tricks your business into sending money to them under false pretenses.
In both cases, the result is lost funds and potential bank fees, not to mention possible damage to your reputation. ACH fraud can be financially devastating for small businesses with tight cash flows. For example, if a fraudulent withdrawal clears out your operating account, you might struggle to make payroll or pay vendors on time.
Compounding the issue, small businesses don’t enjoy the same broad protections as consumer accounts under U.S. law – we’ll discuss the regulatory details later, but the key point is that businesses may have a very short window to detect and report ACH fraud. Failing to act fast could mean you are liable for the loss.
Why is ACH fraud on the rise?
Criminals follow the money, and more payments are shifting to ACH. ACH credit transfers have become a favorite target in sophisticated scams like business email compromise (BEC).
Meanwhile, traditional check fraud still hasn’t gone away (63% of organizations faced check fraud in 2024), but ACH offers cybercriminals a digital route to illicit gains.
Business email compromise, where scammers impersonate a trusted party via email to induce fraudulent payments, led to $2.9 billion in reported losses in 2023 in the U.S. – and much of that was achieved by diverting ACH or wire payments.
For small business owners, caring about ACH fraud isn’t optional – it’s part of modern financial risk management. Even one incident can mean thousands lost, hours of paperwork, and broken trust with customers or suppliers.
In the next sections, we’ll break down how ACH fraud works through common schemes, so you can recognize the red flags and be prepared.
Common Types of ACH Fraud (U.S. Scams and Schemes)
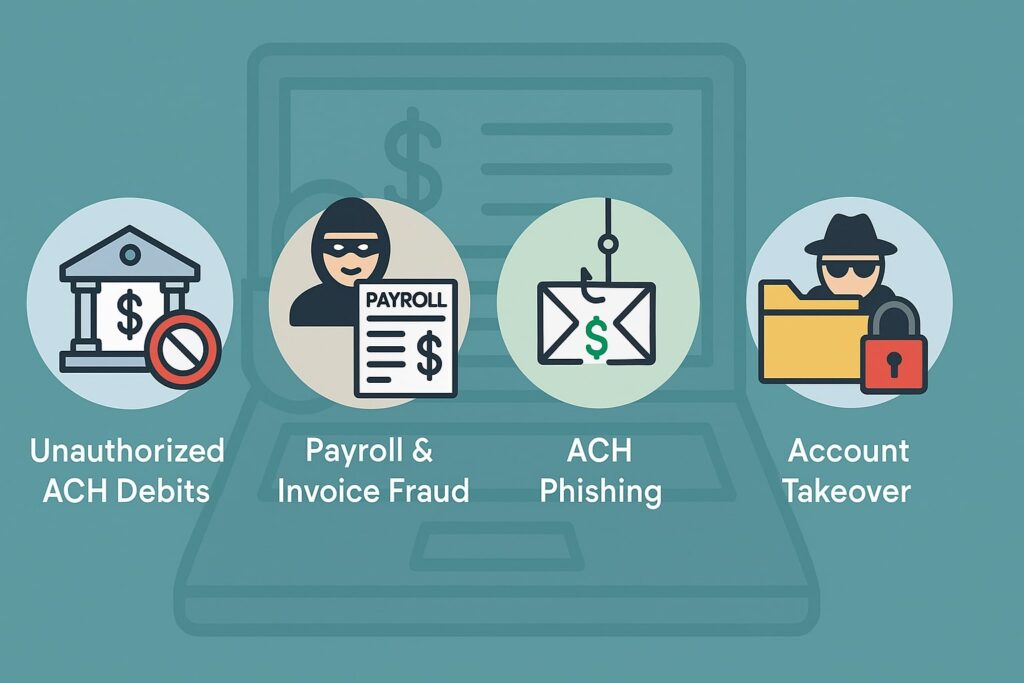
ACH fraud can take many forms. Below is a summary of common ACH fraud types, how they work, and basic prevention tips for each. We’ll then explore each type in more detail:
| Fraud Type | How It Works | Example Scenario | Key Prevention |
|---|---|---|---|
| Unauthorized ACH Debit | Fraudster uses stolen bank account and routing numbers to withdraw funds from your account without permission. | An unknown ACH withdrawal appears on your statement – the thief obtained your account info from a phishing email or a breached check. | Monitor accounts daily; use ACH debit blocks/filters to allow only trusted debits. |
| Account Takeover | Fraudster gains access to your online banking (via stolen credentials or malware) and initiates ACH transfers out of your account. | A hacker logs into your business’s banking portal and sends out payments to their own accounts. | Enable multi-factor authentication (MFA) on bank logins; use strong passwords and updated security software. |
| Business Email Compromise (BEC) | Scammer impersonates a vendor or executive via email (often through phishing) to trick you into changing payment instructions or sending a fraudulent ACH payment. | You receive an email that looks like it’s from a regular vendor, asking to ACH payment to a “new bank account” – but it’s actually a scammer’s account. | Verify requests via a second communication channel (e.g. call the known phone number) before changing payment details; require a secondary approval for new payees. |
| Fake Invoices (Vendor Fraud) | Fraudster sends bogus invoices or alters legitimate ones to divert payments to themselves. Often part of BEC schemes or mail/email scams. | Your accounts payable team pays an invoice that looks legitimate, not realizing the banking details were changed to an imposter’s account. | Confirm invoice details with the vendor directly for any first-time or changed payment information; train staff to spot irregularities in invoices. |
| ACH Kiting | A scammer exploits the float (time gap) in ACH transfers by rapidly moving nonexistent funds between accounts to create artificial balances. | The fraudster sets up accounts at two banks and “circulates” a phantom $50,000 between them via ACH, withdrawing real cash before the fraud is discovered. | Banks use algorithms to detect kiting patterns (e.g. frequent cross-bank transfers). As a business, watch for unexpected incoming funds followed by urgent withdrawal requests. |
| Insider Fraud | An employee or insider with access initiates unauthorized ACH transfers or manipulates account data for personal gain. | A rogue employee with treasury access sends small ACH payments to their own account or a collaborator’s account, hoping it goes unnoticed. | Implement segregation of duties so no single employee can set up and approve an ACH payment; regularly audit and reconcile accounts to catch anomalies. |
Each of these fraud types involves different tactics, but they all result in money leaving your business’s account wrongfully or not reaching the intended party. Let’s dive deeper into how these schemes work and their warning signs.
1. Unauthorized ACH Debits (Fraudulent Withdrawals)
What it is
An unauthorized ACH debit occurs when a fraudster pulls money out of your bank account without your permission.
To do this, the criminal needs your bank’s routing number and your account number – information that might be obtained via phishing emails, data breaches, or even by stealing a check (since U.S. checks have those numbers printed on them).
Armed with these details, the fraudster can masquerade as a payee you supposedly authorized, and initiate an ACH withdrawal (for example, by using an online payment service or submitting an ACH request through a bank).
How it works
The fraudulent transaction might be sneaky or blatant. Sometimes the thief will attempt a small debit (just a few dollars) to test if the account is active, and then follow up with a larger withdrawal.
Other times, they may attempt a large one-time hit. Because ACH transactions don’t always alert you in real time, you could be unaware until you reconcile your bank statement or get an overdraft notice.
Criminals commonly obtain account info through scams or hacks – for instance, a hacker who breached another company’s payroll system might steal account numbers, or a scammer might trick you or your employee into emailing a voided check image.
Real-world scenario
A small retail business owner finds that a $5,000 ACH debit labeled “Vendor Payment” was withdrawn from her account, paid to an unknown entity.
She later discovers a fraud ring obtained her banking details after she fell for a spoofed email requesting account verification. Because she didn’t catch it within a day, recovering the money became difficult.
How to detect & prevent unauthorized debits
As a small business, one of the best defenses is to monitor your bank account daily for any unfamiliar transactions. Most banks offer alerts you can set up for ACH activity. Additionally, ask your bank about ACH debit blocks or filters.
These are treasury management services designed for businesses: you can block all ACH debits except those from approved partners, or set dollar thresholds that trigger manual review. ACH Positive Pay is another service some banks provide – it allows you to pre-authorize specific ACH debits (by company ID and amount).
Any attempted debit that isn’t on your list will be flagged or rejected, providing strong protection against unknown withdrawals. In short, limit who can pull funds from your account. If your business doesn’t use auto-debits at all, a blanket ACH block on your account can be a lifesaver.
Regular reconciliation is also key: compare each day’s cleared ACH transactions against what you expected to happen. The sooner you spot an unauthorized debit, the better your chance of reversing it.
(Under U.S. NACHA rules, business accounts have as little as 24 hours to report and return an unauthorized ACH debit in many cases, whereas consumer accounts have longer protections. This means prompt detection is critical for businesses.)
2. Account Takeover Fraud
What it is
In an account takeover, a fraudster literally takes control of your bank account – typically by stealing your online banking credentials – and then uses that access to initiate payments.
They might send themselves ACH transfers (as ACH credits originating from your account) or even wire transfers and bill payments. Small businesses that do banking via online portals are targets of this cybercrime.
How it works
Cybercriminals use malware, keyloggers, or phishing schemes to capture your company’s bank login ID and password. For example, your bookkeeper might accidentally install malicious software from an email attachment, which then records keystrokes including the online banking password.
Once the attacker has your credentials, they log in – often masquerading as a legitimate user – and can initiate outgoing ACH transfers (often as “ACH credits” or bill pays) to accounts they control.
Because they are in your actual account, these transfers look like authorized transactions from your business. Sophisticated criminals may even change contact details (like email or phone numbers on file) to delay detection of their activity (so that fraud alerts from the bank go to the attacker, not you).
Signs of account takeover
Unfamiliar login notifications, or your account being locked out unexpectedly, could indicate someone else tried to access it. Another red flag is seeing new payees or payments in your transaction history that you or your staff didn’t initiate.
Given that these fraudsters often strike outside normal business hours, you might see ACH batches initiated late at night or on weekends.
Prevention
Strong online banking security is paramount. Always use multi-factor authentication (MFA) for your bank logins. MFA means that even if the username and password are stolen, the thief cannot get in without a second factor (like a one-time code sent to your phone or generated by an app).
Most banks provide MFA – ensure it’s enabled for all users on your account. Additionally, use robust passwords or passphrases and change them periodically.
Protect your devices as well
keep antivirus and anti-malware software updated on any computer or device used for banking. Segregating duties can help too; for instance, use a dedicated computer for financial transactions that isn’t used for everyday web browsing or email, to reduce exposure to malware.
Employee cybersecurity training is essential so staff can recognize phishing attempts and avoid unsafe links. By minimizing the risk of credential theft, you significantly reduce the chance of an account takeover.
If you suspect an account takeover (e.g., you notice unauthorized payments or receive alerts about login from an unknown device), contact your bank immediately and freeze activity. Banks can often claw back or hold ACH transfers if notified quickly.
U.S. regulations also encourage banks to implement security measures; for example, Federal Financial Institutions Examination Council (FFIEC) guidelines urge strong authentication for business banking.
In fact, new 2024 NACHA rules now require all parties in the ACH network – including receiving banks – to monitor and flag suspicious ACH transactions as a way to combat account takeover and BEC fraud. This means your bank might sometimes delay crediting an incoming ACH if it appears suspect, adding an extra layer of protection.
3. Business Email Compromise (BEC) and Impersonation Scams
What it is
Business Email Compromise is a deceptively simple but effective fraud where criminals impersonate a trusted person or business via email to trick you into sending money to the wrong account.
In the context of ACH, BEC often means a scammer convinces you to push an ACH payment to them by pretending to be someone you owe money to (like a vendor or even your boss). This is also known as vendor impersonation or CEO fraud, depending on whom they impersonate.
How it works
Typically, the fraudster begins with a phishing attack to infiltrate or spoof email accounts. They might hack into your vendor’s email system or create an email address very similar to your supplier’s.
Then, they send a message to your accounts payable department that looks legitimate – perhaps an invoice or a request to change the bank account on file for future payments. The email might say something like, “We recently updated our banking details, please send this month’s payment to our new ACH account.”
If your team updates the account info and processes the ACH, the money goes straight to the fraudster’s account. By the time the error is discovered, the funds may have been quickly withdrawn or moved overseas.
Another BEC scenario involves fake invoices (which overlaps with vendor impersonation). The scammer sends an invoice for services/products you didn’t order, hoping your staff will pay it without verification.
Or they intercept a real invoice and alter the bank details before it reaches you. These schemes rely on the human tendency to trust what appears routine.
Why BEC is dangerous
These scams bypass technical firewalls by exploiting human trust and established processes. The emails are often well-crafted, sometimes even referencing real transactions or people gleaned from compromised correspondence.
BEC has become one of the costliest forms of cybercrime – it was the root cause of a majority of payments fraud cases in recent surveys. And small businesses are not immune; in fact, scammers often assume smaller companies may not verify changes as strictly as large corporations.
Prevention
The mantra for defeating BEC is “verify before you pay.” Anytime you receive an email requesting a change in payment instructions, especially for ACH or wire transfers, confirm it through a separate channel.
Call your vendor at the phone number you have on record (not a number in the suspicious email) and ask if they sent that request. 99% of the time, a quick call can expose a fraud attempt.
Train your employees to be skeptical of urgent or secretive requests, especially those urging them to bypass standard procedures.
Implementing a dual-approval process for outgoing ACH payments is highly effective. For example, if one employee initiates a new payee or a transfer above a certain amount, require a second employee (manager or owner) to review and approve it before the bank processes it.
This two-person rule makes it much harder for a single spoofed email to result in an unauthorized transfer. It also creates an opportunity to catch unusual requests (“Why are we paying this unfamiliar account?”).
Email security measures can help as well: use spam filters and phishing awareness training to reduce the chance these scam emails even reach the payable staff. Some companies adopt a policy that any payment instruction change must be verified by phone or a live video call with the vendor.
Considering that 50% of organizations reported ACH transfers were specifically targeted in BEC attacks, these extra steps are well worth it.
4. Fake Invoices and Billing Fraud
What it is
While often tied into BEC, fake invoice fraud can also occur through traditional mail or other channels. Essentially, your business receives an invoice for goods or services that were never delivered or from a company you don’t recognize, or an invoice that looks legitimate but has subtly altered payment details.
If your accounts payable team isn’t careful, they might pay it via ACH, unknowingly sending money to criminals.
How it works
Fraudsters may research your company and identify likely services you use. Then they generate an invoice that looks professional – sometimes even copying logos from real businesses – and bill you for a routine amount.
They often choose relatively small amounts that won’t raise immediate flags (e.g., $300 for “office supplies” or a periodic software subscription), hoping it slips through. Alternatively, they might impersonate one of your real vendors and just change the bank account on the invoice.
If your vendor normally bills you $5,000 monthly, a scammer might send an invoice for $5,050 with “new ACH payment instructions” – banking on the possibility that the overworked accounting clerk will process it without double-checking.
Prevention
Vigilance in accounts payable is the best defense. Establish a procedure for verifying invoices: for any new payee or changed bank account details, require confirmation with the vendor’s known contact (similar to BEC protection).
Maintain an approved vendor list and have managers review payments to any vendor not on the usual list. It’s also wise to rotate duties or have a second pair of eyes audit invoices periodically – fresh eyes can catch what someone who sees invoices every day might miss.
Technology can assist too: accounting software often can flag duplicate invoice numbers or amounts, which might indicate a fake invoice trying to mimic a previous legitimate one.
Encourage employees to question things: an empowered accounts payable clerk should feel comfortable holding up a payment to ask, “Do we really owe this?” In many cases, a simple phone call or email to a known vendor contact will reveal the invoice as fake.
5. ACH Kiting
What it is
Kiting is a fraud scheme historically known with checks, but it has an ACH variation. The perpetrator exploits the time delay in the clearing process to float non-existent funds. Essentially, they play a balancing act by moving money between two or more bank accounts to create an illusion of funds, withdrawing real money before the illusion collapses.
How it works
Suppose a fraudster has two bank accounts at Bank A and Bank B. They initiate an ACH transfer of $50,000 from Bank A to Bank B (this is an ACH debit pulling from A to deposit in B). On day one, Bank B might credit the $50,000 pending final settlement, making it look like account B suddenly has money.
Before the transfer actually clears (which might be later that day or the next), the fraudster quickly initiates another transfer to move $50,000 back from B to A or withdraws funds from B via cash or wire.
If timed right, they can yo-yo funds back and forth – or just cash out – all while each bank temporarily trusts that the other bank will provide the money. Eventually, one of the transfers will bounce due to insufficient funds, revealing that the money never truly existed. By that time, the fraudster hopes to have withdrawn the max amount possible.
Is a business likely to be a victim of kiting?
In many kiting cases, the fraudster is actually the account holder at both banks (using fake or stolen identities to open accounts). In that sense, businesses aren’t typically “tricked” into sending money in a kiting scheme; rather the banks are duped by the float timing.
However, a small business could indirectly get entangled – for instance, if someone pays you with an ACH transfer that is part of their kiting chain, that credit could be reversed when the scheme unravels.
Prevention/detection
Banks have become better at spotting kiting. They use pattern-recognition software to detect rapid-fire in-and-out transfers of round numbers that don’t fit the customer’s normal activity. As a business, if you see an unexpected large ACH credit from an unknown source, be cautious – it could be a mistake or fraudulent.
Don’t immediately spend funds that seem suspicious until they fully clear. Fortunately, kiting is relatively uncommon compared to BEC and phishing, but it’s important to be aware of it as part of the fraud landscape.
6. Insider Fraud (Internal ACH Misuse)
What it is
Not all threats come from outside hackers; sometimes, a fraud risk is on your payroll. Insider fraud involves an employee or contractor using their access to systems or accounts to commit ACH fraud.
This could range from a bookkeeper covertly issuing an unauthorized bonus to themselves, to an IT admin diverting payments by altering account numbers.
How it works
Insiders often exploit trust and inadequate oversight. For example, an employee in the finance department might create a new vendor record in the payment system tied to their own bank account and then initiate an ACH payment to that “vendor.”
Or an employee with access to online banking could simply send themselves an ACH transfer if no one is checking. In some cases, an insider collaborates with an external fraudster (for a cut of the money) by, say, leaving a door open in security or approving a fraudulent payment that would have been flagged.
Prevention
Strong internal controls and a culture of ethics are key. Implement segregation of duties so that no single individual can complete a sensitive transaction from start to finish.
For instance, one person enters or initiates ACH payments, and another person must review and approve them. This makes it much harder for a rogue employee to secretly pay themselves.
Regular job rotation or mandatory vacations can also expose fraud – if someone else takes over an employee’s duties for a week, they might notice irregularities.
Conducting regular audits and reviews of ACH transactions can catch unusual activity. Small businesses should reconcile accounts frequently (daily or weekly) and scrutinize any payments to names or accounts that don’t match known payees.
It’s also wise to use least-privilege access controls: give employees access only to the systems and functions necessary for their jobs. If an employee doesn’t need ACH capability, don’t provide it.
Additionally, background checks for employees handling finances and creating an environment where whistleblowing is encouraged (and protected) can help deter insider schemes.
Fraud awareness training isn’t just for external scams – ensure employees understand that internal fraud is a serious offense with legal consequences. Building a culture of honesty and accountability can go a long way; as the saying goes, “trust, but verify.”
U.S. Regulations, Liability and Protections for ACH Fraud

Understanding your liability in ACH fraud cases is crucial for small business owners. In the United States, the rules and laws that apply to unauthorized electronic transactions differ for consumer accounts versus business accounts, and this affects how losses are handled.
- Consumer vs. Business Protection: Personal bank accounts are covered by the Electronic Fund Transfer Act (EFTA) and Regulation E, which strictly limit a consumer’s liability for unauthorized electronic transactions (including ACH) as long as they report the fraud in a timely manner.
For example, if a thief pulls money from a consumer’s checking account via ACH without authorization, the bank must investigate, and usually the consumer can get reimbursed if they report it within 60 days of their bank statement.
Business accounts, however, are not covered by Reg E. Instead, they fall under the Uniform Commercial Code Article 4A and NACHA operating rules. These put more responsibility on the business to spot and report issues quickly.
In fact, as noted earlier, NACHA rules give businesses as little as one to two banking days to return an unauthorized ACH debit. If you don’t catch it and notify your bank immediately, the bank may not be obligated to recover your funds. - 24-Hour Rule for Unauthorized ACH Entries: When a fraudulent ACH debit hits your business account, you typically have until the end of the next business day to alert your bank and have them initiate a return (this is sometimes called the “24-hour rule”).
A retired attorney writing on the issue bluntly described that small business owners essentially “have just 24 hours to fight back” against unauthorized ACH withdrawals, far less protection than consumers enjoy.
After that window closes, your bank might still try to help, but the onus could be on you to pursue recovery from the perpetrator (often an impossible task). This is why frequent account monitoring is so important for businesses. - Liability for Fraudulent Payments (BEC, etc.): If your employee is tricked by a BEC scam into initiating an ACH payment (meaning the transaction was technically authorized by your company, albeit under false pretenses), liability can be murky.
Generally, if the bank processed the payment as instructed by an authorized user, the bank is not liable – even though you were defrauded. The loss typically falls on the business, unless you can prove the bank failed to follow a security procedure you agreed on.
Many courts have sided with banks in cases where companies were victimized by BEC fraud, especially if the business had declined stronger security options the bank offered. In short, if someone at your company approved the transfer (even fraudulently), the business often bears the loss.
This makes internal controls and employee training your best protection – it’s far better to prevent a fraudulent transfer than to rely on after-the-fact remedies. - Bank and Network Obligations: The ACH network (NACHA) has been implementing new rules to combat fraud. Starting in 2021, NACHA defined time limits (1 year for businesses, 2 years for consumers) for banks to make claims on unauthorized entries, giving originating banks more certainty about liability cut-offs.
More recently, NACHA’s 2024 rules for “credit-push” fraud (like BEC scenarios) empower banks to help recover funds – for example, the originating bank can request the return of a suspicious payment for any reason, and the receiving bank can voluntarily return funds it suspects are fraudulent.
Additionally, receiving banks can delay availability of funds for further review if something looks fishy (within legal limits). While these measures don’t shift liability per se, they aim to improve the odds of stopping fraud in progress and retrieving money.
As a business owner, you should maintain a good relationship with your bank – they can be an ally in fraud prevention. If you report something odd, a good bank will act quickly to investigate and possibly halt transactions or help with recovery through the proper channels. - Insurance: Although not a regulation, it’s worth noting that many businesses obtain cyber liability or crime insurance that can cover certain fraud losses, including ACH fraud.
Policies vary, but if your business has significant exposure, insurance can be a last layer of protection. Just remember, insurance claims will expect that you also had reasonable controls in place.
ACH Fraud Prevention Strategies for Small Businesses

Preventing ACH fraud is far easier than trying to recover money after the fact. Fraud prevention boils down to implementing good security practices, using banking tools effectively, and fostering a vigilant company culture. Here are essential ACH fraud prevention strategies, tailored for small businesses:
- Enable Multi-Factor Authentication (MFA) for Banking: Protect your online bank accounts with MFA so that a password alone isn’t enough to access them.
Even if login credentials are stolen, requiring an extra code or authentication step will thwart most unauthorized access attempts. This simple step greatly reduces the risk of account takeovers. - Use ACH Blocks and Filters: Talk to your bank about ACH fraud protection services such as pre-authorized debit filters or blocks. An ACH debit block can prevent any withdrawal from your account unless pre-approved.
Filters can allow you to specify approved trading partners and dollar limits. These tools ensure that any ACH debit deviating from your criteria is flagged for review or automatically rejected, stopping fraudulent withdrawals before they occur. - Set Alerts and Monitor Accounts Daily: Set up real-time alerts for ACH transactions on your accounts (most banking portals let you get text or email notifications for any ACH above a certain amount).
Daily monitoring and quick reconciliation will help you catch suspicious items immediately. The faster you spot fraud, the more likely you can reverse it. - Dual Control for Payments: Implement a policy that at least two people must be involved in releasing significant ACH payments or adding new payees. This could mean one employee enters the payment and another approves it in the banking system.
Dual approval makes it much harder for a single mistake or malicious act to result in an unauthorized transfer. It’s a critical control, especially for wire or ACH transfers over a threshold (e.g., any ACH over $5,000 requires manager sign-off). - Segregation of Duties: Beyond just dual approval, ensure that financial duties are divided among staff. The person reconciling the bank account, for example, should not be the same person who issues payments.
Splitting responsibilities creates natural checks and balances that can catch errors or fraud. For a very small business with one finance person, the owner or an external accountant should review the transactions regularly. No one person should have free rein over all aspects of payments. - Train Employees on Fraud Awareness: Your staff are the first line of defense. Conduct regular training on how to recognize phishing emails, social engineering tricks, and suspicious requests.
Teach them that fraudsters often pose as trusted partners or authorities and pressure people into bypassing normal procedures. Encourage a healthy skepticism – it’s better to verify an odd request than to assume it’s fine.
Employees should know to double-check unsolicited emails about payments, and to never reveal passwords or sensitive info via email. Frequent reminders and even phishing simulation tests can keep awareness high. - Secure Your IT Environment: Cybersecurity and ACH fraud prevention go hand in hand. Ensure all computers and devices that handle financial information have updated antivirus/anti-malware protection.
Keep operating systems and software patched to fix vulnerabilities that hackers could exploit. Use firewalls on your network and secure your Wi-Fi (use strong encryption and passwords) to prevent unauthorized network access.
If possible, limit online banking activities to a dedicated, secured computer. Regularly back up important data in case of ransomware or destructive attacks. Essentially, close the digital doors that intruders might use to get to your financial info. - Use Secure Payment Systems and Gateways: If you pull ACH payments from customers or use payment software, choose providers with robust security (encryption, fraud detection).
For instance, using a reputable payment gateway or service (like PayPal, Stripe, etc.) can add layers of fraud screening and encryption to transactions. These providers often have tools to verify bank accounts and detect anomalies, which can supplement your own efforts. - Limit Exposure of Bank Info: The fewer places your bank account details appear, the better. Avoid printing your account and routing numbers on publicly viewable documents. Be cautious about sharing banking info via email; use secure channels when providing vendors with your ACH details.
Also consider having a separate account for ACH transactions – for example, you might keep most funds in a core account and transfer funds into a dedicated ACH payment account only when needed. This way, even if that ACH account’s details are compromised, the fraudster can’t empty your entire treasury. - Set Transaction Limits: Many banks allow you to set limits on ACH transfers (per transaction or per day). If your typical ACH payments are, say, under $10,000, you might set a hard cap that no ACH can exceed $10k without special permission.
Similarly, you could arrange with your bank to require a call verification for any ACH above a certain size. While this might not be offered everywhere, it’s worth asking about.
Internal software can also enforce limits – preventing an entry above a threshold from even being initiated without higher approval. - Real-Time Fraud Monitoring Tools: Consider using services or software that employ machine learning and pattern analysis to watch your transactions.
These systems establish a baseline of your normal payment activity and can flag unusual transactions (like a payment to a new recipient or a spike in amount) for review.
Some banks provide this as part of their treasury services, or you can subscribe to third-party solutions. While a small business might not have a dedicated fraud team, technology can act as a 24/7 watchdog and even halt suspicious transfers pending your approval. - Regular Reconciliation and Audits: Establish a routine to reconcile your bank accounts frequently and review ACH payments. At minimum, do a thorough review at month-end, but in higher risk periods, weekly or daily checks are better.
Also, periodically audit your payment processes and user access rights. An independent review (by a manager or external accountant) of who has ACH access and how controls are working can reveal gaps before a fraudster finds them.
For instance, you might discover an old employee’s login is still active – a potential security hole that should be closed. - Plan for Incident Response: Despite best efforts, things can go wrong. Have a plan for what to do if you suspect or confirm ACH fraud.
This should include: who to contact at your bank (have their fraud hotline or rep’s number handy), how to temporarily freeze transactions, and whom internally to alert (ownership, finance, IT).
Also, know the steps to file a police report or FBI Internet Crime Complaint Center (IC3) report if needed. Time is critical in responding – banks can attempt to reclaim funds from the receiving bank if alerted very quickly.
Having a response playbook ensures no time is wasted figuring out next steps under stress. It’s better to have a plan and never need it than scramble in the moment. - Collaborate with Your Bank and Partners: Finally, maintain open communication with your financial institutions. They can advise you on the latest fraud prevention offerings and may have proactive monitoring on their side that can complement your efforts.
For example, some banks will call you if they see an unusual ACH from your account. Respond promptly to any such inquiries.
If you use payment processors or payroll services, inquire about their security measures and ensure they follow industry standards to protect your data (since a breach in their system could lead to ACH fraud against you).
By implementing these layered strategies – combining technology tools, process controls, and employee awareness – you create a strong defense against ACH fraud.
It’s much like securing a house: you want locks on the doors (passwords/MFA), alarms for break-in attempts (alerts/monitoring), rules for who holds keys (access controls), and good habits like checking that the doors are closed (reconciliation).
No single tactic is foolproof, but together they significantly reduce the likelihood of fraud and increase the chances of catching it early.
Frequently Asked Questions (FAQs)
Q: How can someone steal money from my account with just my account and routing number?
A: In the U.S., those two numbers are essentially the keys to initiate an ACH withdrawal (or to print a check). Criminals who obtain your bank account number and routing number can attempt ACH debits claiming you authorized it.
Banks assume ACH requests are legit if they come through proper channels. That’s why protecting your account info and using ACH blocks/filters is so important.
Q: What should I do if I discover an unauthorized ACH transaction on my business account?
A: Act immediately. Contact your bank’s fraud department or your relationship manager and report the unauthorized ACH debit. Instruct them that it’s fraudulent and request an ACH return. Time is critical – try to report it within 24 hours of it posting.
The bank will likely have you fill out a Written Statement of Unauthorized Debit. Also, check if there are any other suspicious transactions, change your online banking password, and review security practices to plug any holes that allowed the fraud.
Q: Are small business accounts protected from ACH fraud in the same way consumer accounts are?
A: No – business accounts do not get the full protections of Regulation E (which protects consumer accounts). Banks often hold businesses to higher standards. For unauthorized ACH debits on a business account, you typically have only 1-2 days to report and return the item.
If an employee is tricked into sending an ACH (BEC scam), the bank may consider it an authorized payment, leaving the business to bear the loss. Some banks offer additional fraud assistance, but as a baseline, businesses must be much more proactive in preventing and catching fraud.
Q: How is ACH fraud different from wire fraud or check fraud?
A: All are methods to steal money, but they differ in process. Wire fraud often involves tricking someone into sending an irrevocable wire transfer (wires move faster and once sent, they’re very hard to recover).
Banks usually have strong verification for wires, so scammers more often use social engineering (like BEC) to get wires sent. ACH fraud typically exploits the easier access to the ACH network – less upfront verification, using account numbers.
ACH transfers can sometimes be reversed if caught quickly, unlike wires. Check fraud involves stealing or faking paper checks – still very common, as 63% of organizations reported check fraud incidents in recent times.
Check fraud might be forging signatures, altering amounts, or depositing fake checks. For a small business, ACH fraud and check fraud both stem from exposing your bank info (since your account number is on checks), but ACH fraud is entirely digital.
It’s wise to protect against all these fraud types with good banking practices and account monitoring.
Q: Will my bank call me if they see a suspicious ACH on my account?
A: Some banks might, but do not rely on it. Banks do employ fraud monitoring, and with new rules, receiving banks are taking a more active role in flagging suspicious incoming ACH credits. Your bank might contact you if, say, a very large or out-of-pattern ACH hits your account.
However, you should assume that it’s ultimately on you to catch unauthorized transactions. Set up your own alerts and regularly review your statements. If you have a good relationship with your banker, you can ask what fraud detection they offer and ensure your contact info is up to date in case they need to reach you quickly.
Q: Does having ACH fraud happen mean my bank account was “hacked”?
A: Not necessarily. In most ACH fraud cases, the ACH network and your bank’s core systems weren’t breached – instead, the fraud happened through social engineering or stolen information.
For example, if someone emails a fraudulent payment request that your team unknowingly fulfills, the bank just processed what appeared to be an authorized transaction. Or if a criminal got your account number from a discarded check, they can create an ACH request.
These scenarios don’t involve hacking the bank directly. That said, if you do experience ACH fraud, you should also evaluate whether your own systems (email, computers) might have been compromised, since malware or email account hacks can be a precursor to fraud.
Q: Can ACH credits (payments I receive) be fraudulent?
A: Yes, there are a couple of angles. One is the overpayment or refund scam – a fraudster might send a small business an ACH credit (payment) seemingly by mistake, then contact you pretending to be a customer who overpaid and ask for a refund.
Later, the original ACH could be reversed as unauthorized or from a stolen account, leaving you out of pocket if you sent back money. Always wait for payments to fully clear and investigate unexpected ones.
Another angle is if your business is unknowingly dealing with a fraudulent party, you might receive payments that later turn out to be fraudulent (for instance, if someone pays you with money from a hacked account, that payment could get clawed back).
Treat large or odd incoming ACH credits with caution – verify with the sender if possible. In general, while most ACH fraud involves money going out, being cautious with money coming in will protect you from related scams.
Conclusion
ACH fraud is a serious but manageable risk for U.S. small businesses. Cybercriminals and scammers are continually adapting, targeting the ACH network not by breaking its encryption, but by preying on human error, trust, and process gaps.
They may steal account numbers, infiltrate emails, or even manipulate your own staff. The stakes are high – lost money, operational disruption, and potential liability for the business. However, as we’ve detailed in this guide, there are concrete steps you can take to dramatically reduce your exposure to ACH payment fraud.
To recap, knowledge and vigilance are your best allies. Educate yourself and your team about how ACH fraud works – from unauthorized debits to sophisticated BEC scams – so suspicious activities can be spotted in time.
Use the tools at your disposal: implement multi-factor authentication, banking protections like ACH blocks, and internal controls like dual approvals. Stay disciplined about monitoring your accounts and verifying requests, even when things get busy. It’s often the extra phone call or the second glance that prevents a costly mistake.
Remember that while U.S. laws offer some recourse, especially for consumers, small businesses must largely fend for themselves when it comes to fraud prevention. Don’t rely on after-the-fact remedies; focus on preventing fraud and detecting it early.
By doing so, you’ll not only protect your bottom line but also sleep better knowing that the funds you’ve worked hard for are safe.
In the ever-evolving battle against fraud, even modest investments in security can pay off immensely. Stay informed about current threats, keep your defenses up to date, and foster a culture of caution and accountability.
With the right approach, you can enjoy the convenience of ACH payments while keeping ACH fraud at bay.
Empower yourself with the knowledge and tools discussed above, and you’ll significantly strengthen your small business’s ACH fraud protection. Stay safe and proactive!
Leave a Reply